Our overarching goal is to secure decentralized systems and design intelligent autonomous agents that can operate reliably in adversarial, resource-constrained, and safety-critical environments. We approach this by combining blockchain security analysis, machine learning–driven cybersecurity, and reinforcement learning for autonomous UAVs.
Our research sits at the intersection of systems security and artificial intelligence. On one hand, we investigate emerging vulnerabilities in blockchain Layer-2 systems and propose defense frameworks grounded in game theory and AI. On the other, we design intelligent UAV navigation, energy harvesting, and intrusion detection systems that adapt under hostile or uncertain conditions.
Here are some themes and techniques that we currently work on:
Blockchain Layer-2 Security. 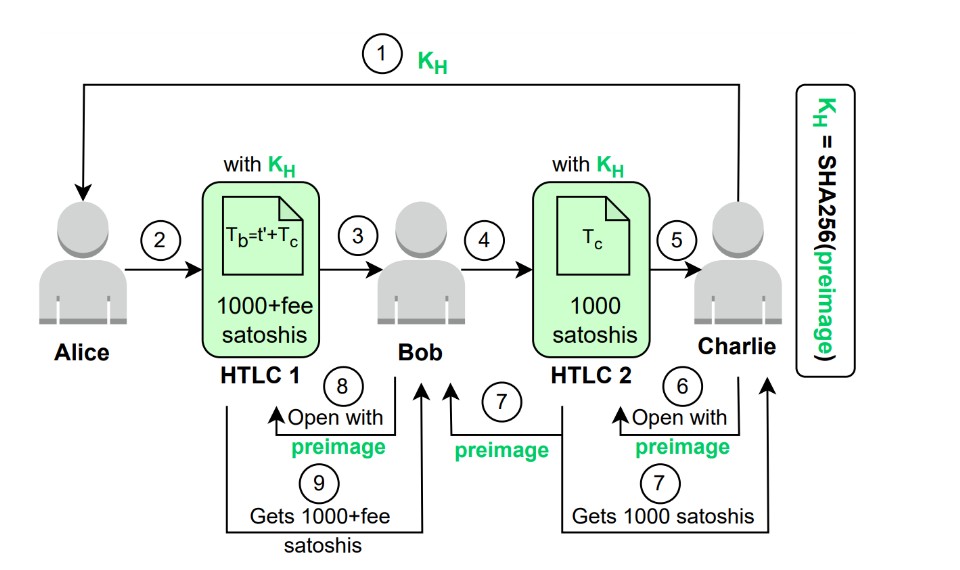 Public blockchains like Ethereum provide strong security guarantees but suffer from scalability limitations, which has led to the rise of Layer-2 (L2) solutions such as optimistic rollups and payment channel networks. While these systems improve throughput and reduce transaction costs, they introduce new and underexplored security vulnerabilities. Our research systematically investigates these weaknesses, including RPC-based state manipulation attacks, arbitrage exploits in ERC-721 token transactions, Sybil attacks in shard-based systems, and fake hashed key attacks on payment channels. To address these threats, we design defense mechanisms that combine graph-based AI models for anomaly detection, Bayesian game theory for strategic validator behavior, and cryptographic safeguards to ensure fairness and reliability. Through this line of work—highlighted by our systems xPoz-Hub, OptiGame, RollGuard, PAROLE, and FAKey—we aim to make L2 blockchains not only scalable but also secure, dependable, and economically robust, paving the way for their safe adoption in decentralized finance, supply chains, and other critical infrastructures.
Public blockchains like Ethereum provide strong security guarantees but suffer from scalability limitations, which has led to the rise of Layer-2 (L2) solutions such as optimistic rollups and payment channel networks. While these systems improve throughput and reduce transaction costs, they introduce new and underexplored security vulnerabilities. Our research systematically investigates these weaknesses, including RPC-based state manipulation attacks, arbitrage exploits in ERC-721 token transactions, Sybil attacks in shard-based systems, and fake hashed key attacks on payment channels. To address these threats, we design defense mechanisms that combine graph-based AI models for anomaly detection, Bayesian game theory for strategic validator behavior, and cryptographic safeguards to ensure fairness and reliability. Through this line of work—highlighted by our systems xPoz-Hub, OptiGame, RollGuard, PAROLE, and FAKey—we aim to make L2 blockchains not only scalable but also secure, dependable, and economically robust, paving the way for their safe adoption in decentralized finance, supply chains, and other critical infrastructures.
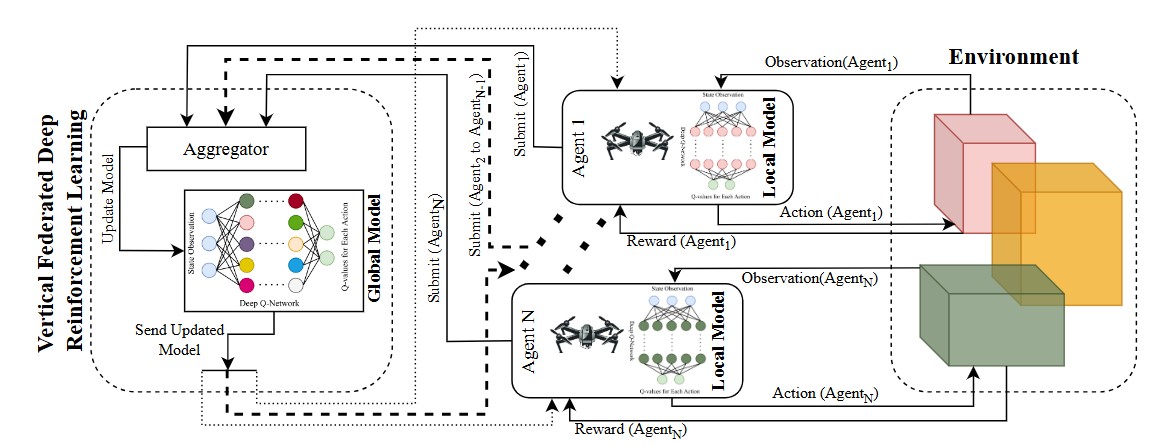
AI-Enabled UAV Path Planning and Security..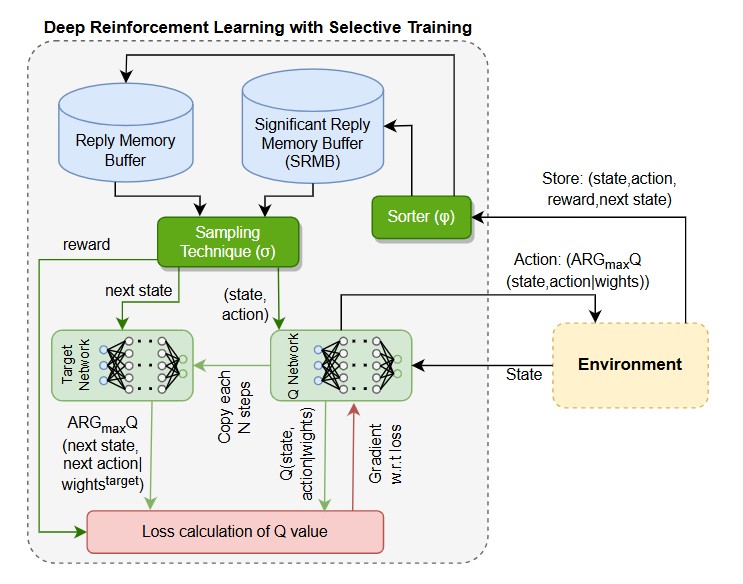 Autonomous UAVs face adversarial challenges such as hostile defense systems and cyber intrusions. We design federated deep reinforcement learning (FedRL) and economic RL methods to enable resilient trajectory planning for individual UAVs and swarms. In parallel, we develop lightweight intrusion detection systems (IDSs) using neuro-fuzzy inference systems (ANFIS) and PWM-signal analysis, enabling secure UAV navigation with low computational overhead.
Autonomous UAVs face adversarial challenges such as hostile defense systems and cyber intrusions. We design federated deep reinforcement learning (FedRL) and economic RL methods to enable resilient trajectory planning for individual UAVs and swarms. In parallel, we develop lightweight intrusion detection systems (IDSs) using neuro-fuzzy inference systems (ANFIS) and PWM-signal analysis, enabling secure UAV navigation with low computational overhead.
Energy Harvesting for UAVs and IoT Systems. Sustainable autonomous systems require self-sufficient energy solutions. We propose RIS-assisted UAVs and cell-free massive MIMO deployments to enable RF energy harvesting for IoT devices. These methods couple advanced communications theory with deep learning optimization to extend operational lifetime in UAV and CPS deployments.
Cyber-Physical Systems (CPS) Security.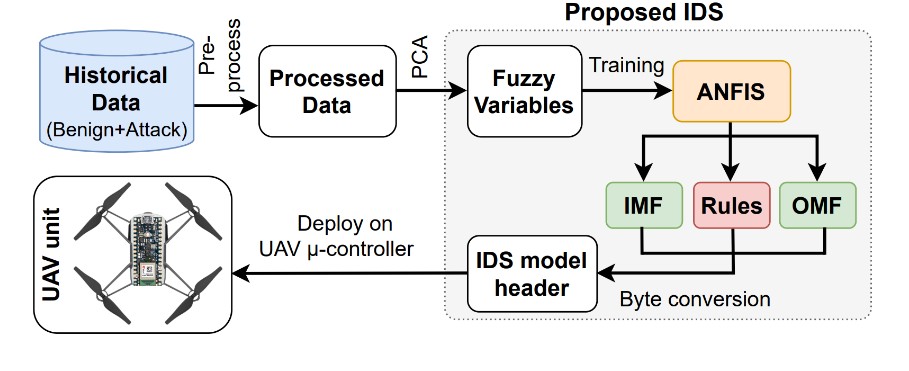 We investigate data-driven anomaly detection and false data injection attacks in CPS domains such as smart grids and digital healthcare systems. Our approaches combine bio-inspired optimization, deep learning classifiers, and blockchain-based auditing mechanisms. By bridging control theory, AI, and blockchain, our work provides resilience in critical infrastructure systems.
We investigate data-driven anomaly detection and false data injection attacks in CPS domains such as smart grids and digital healthcare systems. Our approaches combine bio-inspired optimization, deep learning classifiers, and blockchain-based auditing mechanisms. By bridging control theory, AI, and blockchain, our work provides resilience in critical infrastructure systems.
Federated & Privacy-Aware Learning. A cross-cutting theme is the design of federated AI systems that respect privacy and operate securely across distributed, adversarial environments. Our provisional patent on federated DRL-assisted UAV trajectory planning highlights the potential of privacy-preserving collaborative learning in mission-critical applications.