For a full list of publications, see below. Some of the papers are also available on arXiv.
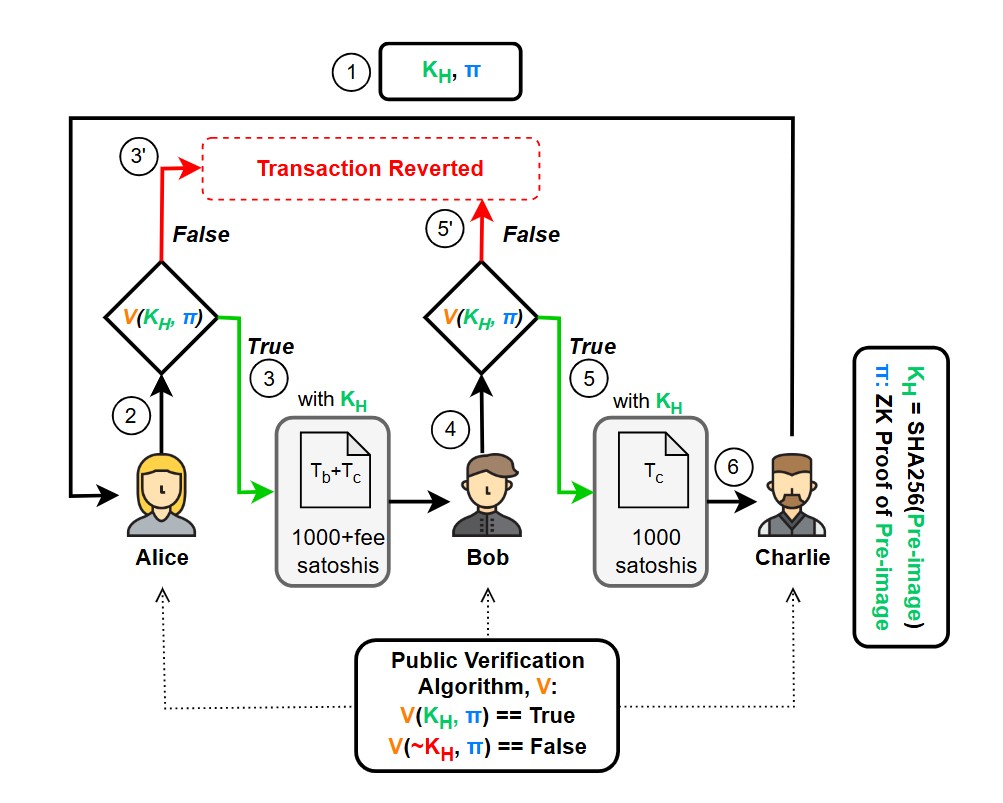
Payment Channel Networks (PCNs) enhance blockchain scalability by enabling off-chain transactions. How ever, the security of PCNs remains a critical concern, particularly in the presence of incentive-based attacks that manipulate the operation of hashed timelock contracts (HTLCs). The recently identified FAKey attack exploits the lack of hashed key ver ification, allowing a malicious sender to use a fake hashed key in HTLCs, thereby locking liquidity, disrupting network throughput, and depriving intermediary nodes of fees. This paper proposes a non-interactive zero-knowledge proof (NIZKP) based secure hashed key verification mechanism to mitigate such attacks. Our approach ensures that intermediate nodes verify the authenticity of the hashed key without revealing the preim age, preventing attackers from injecting fraudulent keys. We design a zk-SNARK-based verification protocol that introduces minimal computational overhead while maintaining transaction privacy and atomicity. Through simulations on PCNsim and real-world analysis of Bitcoin Lightning Network snapshots, we demonstrate that our solution effectively prevents FAKey attacks, reduces failed transactions, and ensures liquidity availability. Furthermore, we analyze the computational feasibility, network adoption challenges, and cryptographic security guarantees of the proposed approach. Our findings suggest that NIZKP-based hashed key verification is a scalable and efficient countermeasure against adversarial manipulation in PCNs.
Alvi Ataur Khalil and Mohammad Ashiqur Rahman
Submitted to IEEE Transactions on Dependable and Secure Computing (TDSC) [Under Review].
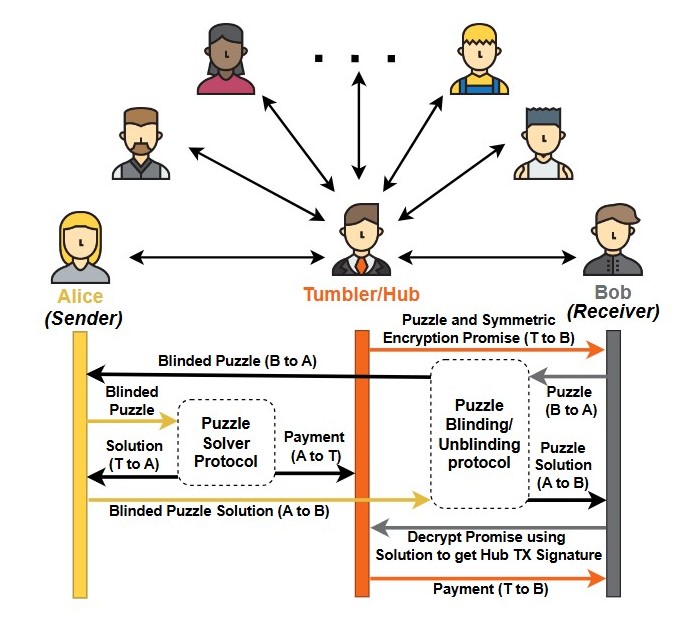
In the ever-evolving realm of blockchain technology, payment channels have become crucial for achieving compet itive throughput. Payment channel network (PCN) was the initial attempt to ease blockchain congestion by enabling off chain transactions through a network of payment channels. However, routing paths in PCNs can become excessively long, leading to high fees and delays. Payment channel hubs (PCHs) address this issue using a central entity (known as the tum bler) to facilitate quick and cost-effective transactions. While facilitating PCH transactions, the tumbler cannot access infor mation, such as the sender or receiver identity or transaction amount. Despite these benefits, PCHs are vulnerable to bal ance discovery attacks (BDAs) due to channel capacity-driven transaction processing, which is fundamental to any system utilizing payment channels. In this work, we propose XPOZ HUB, a novel attack technique designed to expose transactions occurring within the PCH system. Our approach involves a set of collaborative probers that exploit information leaks in PCH response messages to infer sensitive user information (i.e., balance) in an economic and stealthy way. The attackers further collude with the tumbler to access user interaction data, which is leveraged to formulate a constraint satisfaction problem (CSP). By solving this CSP, aided by deep learning (DL)-based transaction pattern identification and incorporat ing insights from BDA reconnaissance, the attackers uncover PCH transactions with high accuracy. We assessed the attack impact by extending the TumbleBit protocol to create a PCH simulator and experimented with PCH mainnet snapshots to illustrate real-world effects.
Alvi Ataur Khalil and Mohammad Ashiqur Rahman
2025 Annual Computer Security Applications Conference (ACSAC 2025)
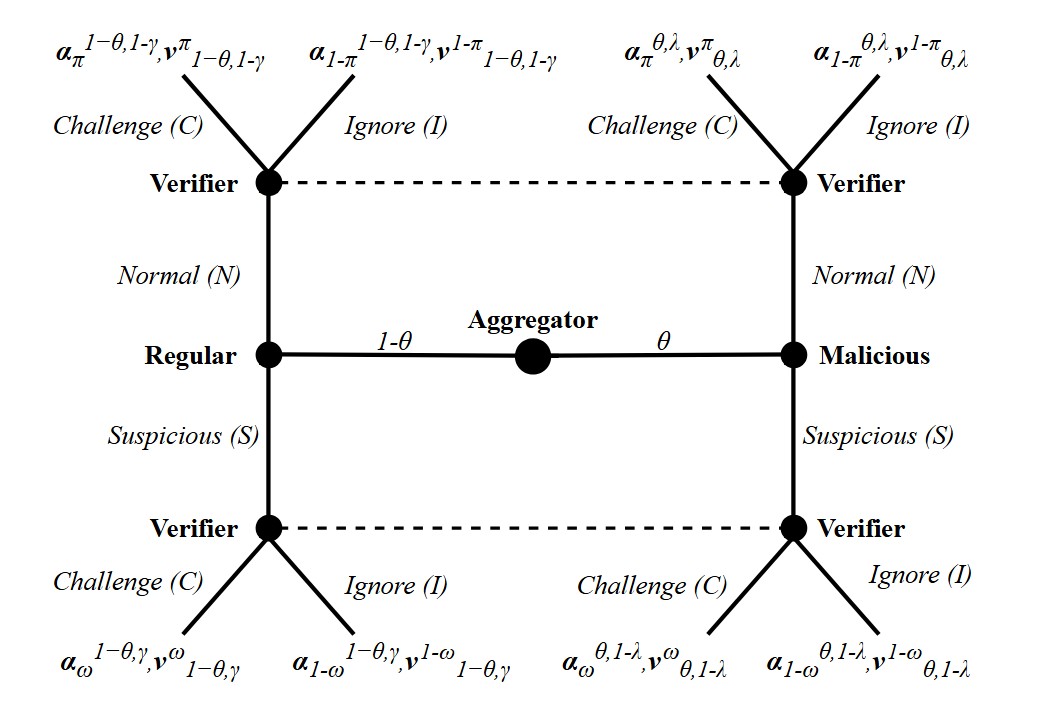
Despite revolutionizing financial transactions, blockchain technology faces critical scalability challenges, impeding its global adoption. Optimistic rollup, a state-of-the-art Layer 2 (L2) scaling solution, ad dresses scalability issues by assuming transaction validity unless challenged. Through this work, we formally identify that interactions within optimistic rollup systems inherently constitute an inspection game be tween aggregators and verifiers, which is vulnerable to adversarial be haviors, as rational aggregators may act dishonestly for illicit gains, while verifiers often avoid challenges to prevent slashing penalties. To address these vulnerabilities, we propose OptiGame, an enhanced pro tocol incorporating a Bayesian game model and a reputation mechanism to strengthen optimistic rollup systems. Our approach incentivizes hon est aggregator behavior and mitigates verifier losses (due to slashing) by aligning economic incentives with security requirements. The proposed model leverages symbolic mathematics to construct an initial mutable payoff matrix based on system parameters and dynamically updates it in response to players’ interactions. To validate OptiGame ’s effective ness in real-world scenarios, we deploy it on the Optimism Sepolia testnet and analyze various performance metrics.
Alvi Ataur Khalil, Md Golam Moula Mehedi Hasan and Mohammad Ashiqur Rahman
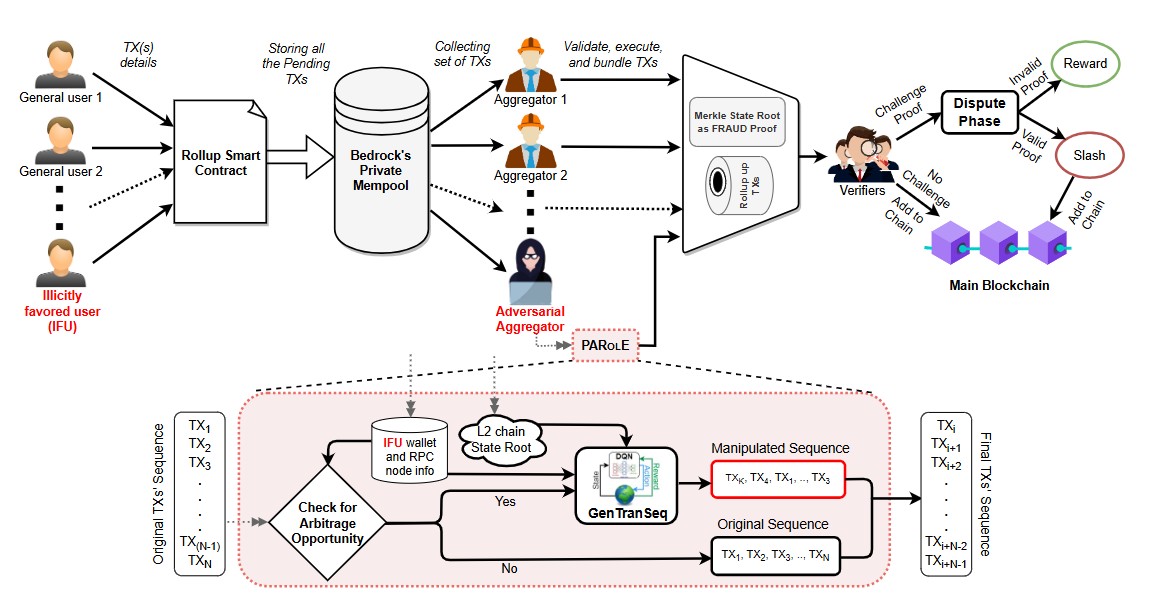
Optimistic rollup has emerged as a promising Layer 2 (L2) scaling solution for blockchain; however, its existing protocols are vulnerable to front/back-running activities, where an opportunistic rollup operator can strategically alter the transactions’ order to create an arbitrage opportunity. Specifically, in the limited edition ERC-721 standardized non-fungible tokens (NFTs), the re-ordering of transactions introduces a lucrative threat landscape due to its scarcity-driven pricing and market volatility. In this work, we introduce PAROLE, a novel attack technique on optimistic rollup systems, where an adversarial aggregator re-orders the NFT transactions in an optimal way, leveraging model-free deep reinforcement learning (DRL) to maximize the balance of a target account. We create our own NFT called the “PAROLE Token” (PT) and deploy it in the OpenSea marketplace via Optimism Goerli to validate the attack impact. Furthermore, we collect NFT snapshots from rollup mainchains to analyze the impact in real-world NFT marketplaces.
Alvi Ataur Khalil and Mohammad Ashiqur Rahman
54th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN 2024)
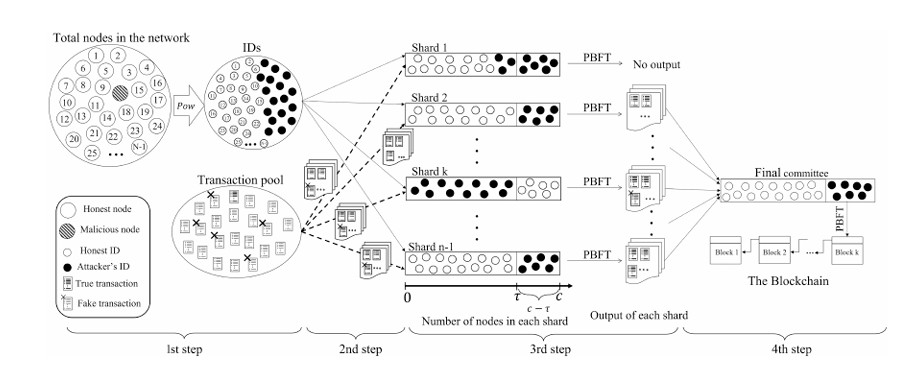
Committee-based permissionless blockchain approaches overcome single leader consensus protocols’ scalability issues by partitioning the outstanding transaction set into shards and selecting multiple committees to process these transactions in parallel. However, by design, shard-based blockchain solutions are vulnerable to Sybil attacks. An adversary with enough computational/hash power can easily manipulate the consensus protocol by generating multiple valid node identifiers/IDs (i.e., multiple Sybil committee members).Despite the straightforward nature of these attacks, they have not been systematically investigated. This article fills this research gap by analyzing Sybil attacks in shard-based consensus of proof-of-work blockchain systems. Specifically, we provide a detailed analysis for Elastico, one of the prominent shard-based blockchain models. We show that the proof-of-work technique used for ID generation in the initial phase of such protocols is vulnerable to Sybil attacks when an adversary (could be a group of colluding nodes) possesses enough hash power. We analytically derive conditions for two different Sybil attacks and perform numerical simulations to validate our theoretical results under various parameters. Further, we utilize the BlockSim simulator to validate our mathematical computation, and results confirm the correctness of the analysis.
Tayebeh Rajabi, Alvi Ataur Khalil, Mohammad Hossein Manshaei, Mohammad Ashiqur Rahman, Mohammad Dakhilalian, Maurice Ngouen, Murtuza Jadliwala, and A Selcuk Uluagac
ACM Journal on Distributed Ledger Technologies - Research and Practice 2023
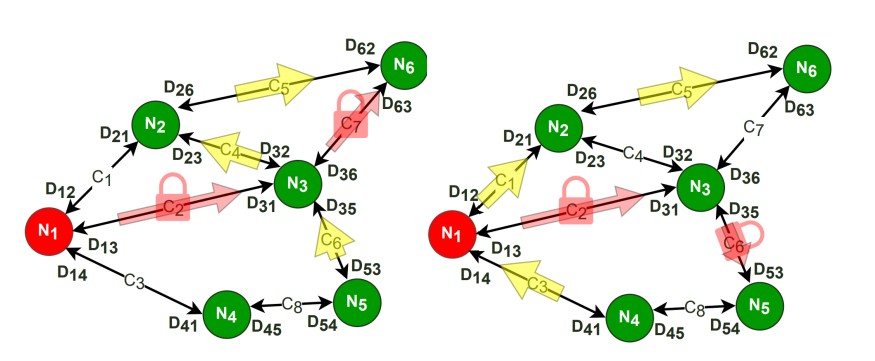
Although blockchain’s immutability and decentralized capabilities make monetary transactions more secure than ever, its inherent scalability problem hinders its utilization in myriad applications. Payment channel networks (PCNs), one of the prominent solutions to blockchain’s scalability issue, reduce the load on the blockchain by performing the transactions offchain. However, malicious PCN participants can delay the block delivery by slightly misbehaving in the initialization phase. In this work, we introduce FAKEY, a fake hashed key-based attack on PCN that can block up a whole set of channels carrying a transaction for a certain period (via collateral lock), depending on the hashed timelock contract (HTLCs) in the attacked payment path. For the targeted attack setup, the effect of the FAKEY is more severe, as PCN throughput can be reduced significantly. Moreover, the attacker can gain direct monetary benefit by carefully choosing one or more victim nodes. We utilize one of the state-of-the-art PCN simulators, PCN sim, to perform multiple experiments with different attack strategies and calculate profit accumulation scenarios. To demonstrate the attack impacts in detail, we perform a couple of case studies using the simulator. Finally, to validate the attack effect and adversarial benefits in a real-world PCN, we utilize the Bitcoin Lightning Network snapshots spanning over a period of 18 months and calculate the exact monetary impact in satoshi units.
Alvi Ataur Khalil and Mohammad Ashiqur Rahman
2023 IEEE Conference on Communications and Network Security (CNS 2023)
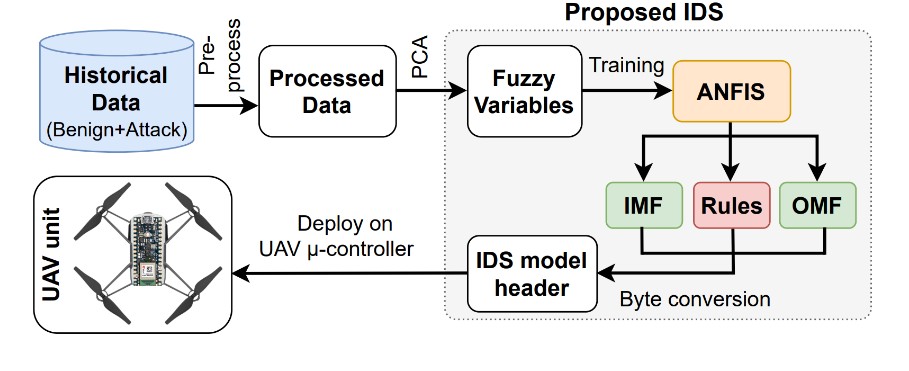
Unmanned aerial vehicles (UAVs) are widely utilized in myriad domains due to their low infrastructure cost and flexibility in deployment. Hostile and unsafe networking environments can make UAVs vulnerable to various attacks. Intrusion detection systems (IDSs) have been developed to detect such attacks. However, conventional data-driven IDSs can be architecturally complex and computationally intensive for resource-constrained small UAVs. In this work, we propose a lightweight IDS for UAVs leveraging an adaptive neuro-fuzzy inference system (ANFIS) that combines artificial neural networks (ANNs) and fuzzy deduction frameworks. Due to the simplistic membership and rule-based classification capabilities of ANFIS, our proposed IDS is lightweight and perfectly suitable for small UAVs. We evaluate the ANFIS-IDS’s effectiveness by comparing its performance to conventional data-driven classification models. In particular, we contrast the proposed IDS with a traditional novelty-based IDS for UAV sensor attacks. We further compare their deployment in a hardware-emulated UAV testbed, assessing the proposed model’s lightweight nature.
Alvi Ataur Khalil and Mohammad Ashiqur Rahman
2023 IEEE 48th Conference on Local Computer Networks (LCN 2023)
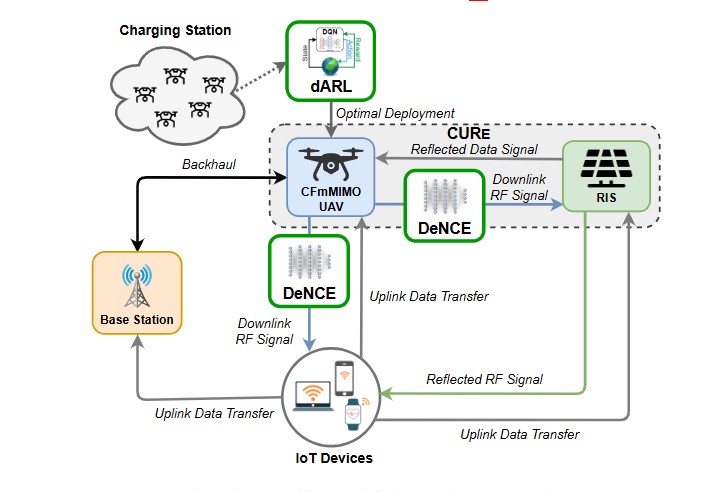
The ever-evolving internet of things (IoT) has spawned hundreds of wireless sensors that communicate via the internet infrastructure. The lifetime and self-sustainability of these sensors are pivotal factors dictating the performance of respective application infrastructure. Radio frequency energy harvesting (RFEH) technology has exhibited the capability of effectively augmenting the battery lifetime of these sensors. In this work, we introduce a novel framework called CURe, which combines the advantages of cell-free massive multiple-input multiple-output (CFmMIMO) and reconfigurable intelligent surfaces (RISs) to provide uninterrupted energy harvesting for IoT devices through RFEH. CFmMIMO integrates the advantages of distributed systems and massive MIMO, while RIS improves the signal strength of the information transfer and RFEH via its passive reflection capabilities. Moreover, we consider unmanned aerial vehicles (UAVs) equipped with CFmMIMO as mobile access points (APs) to better serve the moving sensory devices. To further enhance RFEH, we propose DeNCE, a channel estimation technique based on deep learning (DL) that eliminates the need for traditional closed-form equation-based channel estimation methods. Through evaluation, we first validate the performance of CURe by comparing it with the modified bisection search for max–min fairness (MBS-MMF) algorithm and later corroborate that DeNCE significantly improves the performances of both models. Finally, to optimize the UAV deployment and ensure continuous RFEH coverage, we propose dARL, a deep reinforcement learning (DRL)-based scheduling framework that enables UAV-CFmMIMO swarms to perform continuous energy harvesting in the coverage area collaboratively.
Alvi Ataur Khalil, Mohamed Y. Selim, and Mohammad Ashiqur Rahman
Elsevier Computer Networks (Volume 229, June 2023, 109784) 2023
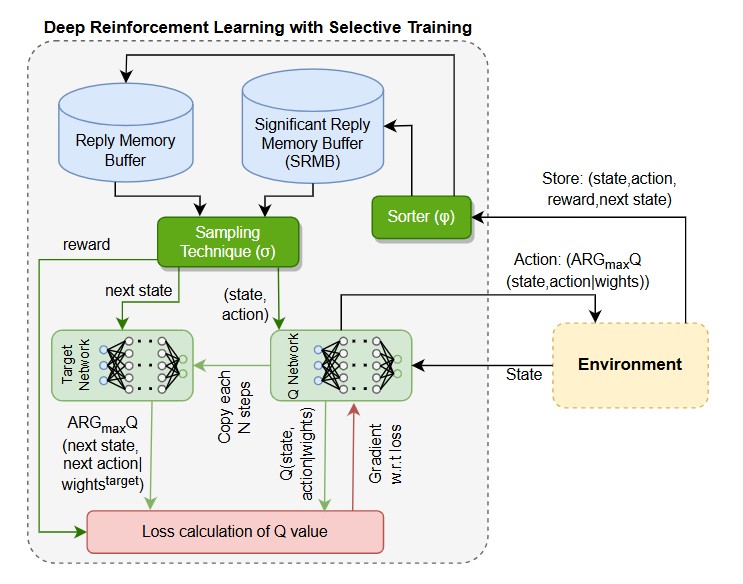
In military operations, unmanned aerial vehicles (UAVs) have been heavily utilized in recent years. However, due to the antenna installment regulation, UAVs cannot be controlled by human operators in a restricted area. Hence, artificial intelligence (AI)-driven UAVs are the practical solution to this out-of-coverage problem. With the increased use of autonomous UAVs in military applications, defense systems are deployed to target and shoot down the enemy UAVs in operation. Thus, UAVs are needed to be trained, not only to achieve goals but also to avoid static and dynamic hostile defense systems. In this work, we propose FED-UP, a federated deep reinforcement learning (DRL)-based UAV path planning framework, that enables UAVs to carry out missions in a hostile environment with a dynamic defense system. The federated learning (FL) based training accelerates the reinforcement learning process and improves model performance. We additionally introduce significant reply memory buffer (SRMB) to quicken the training process more, by selecting the crucial experiences during the training period. The experimental results validate the efficiency of the proposed model in controlling UAVs in dynamic, hostile environments.
Alvi Ataur Khalil and Mohammad Ashiqur Rahman
18th International Conference on Network and Service Management (CNSM 2022)
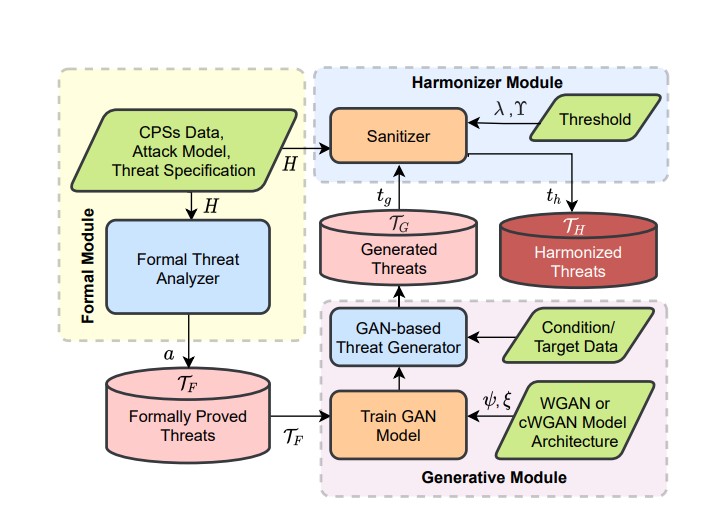
As cyber-physical systems (CPSs) become an essential part of critical infrastructures and industries, their technological advancement creates a massive space for adversaries. Therefore, it is crucial to sufficiently explore the threat space to assess the systems’ resiliency and plan for hardening. Moreover, due to any change in the cyber, physical, or operational level, CPSs often demand a re-analysis of potential threats. Threat analysis by conducting testbed experiments helps comprehend the attack potentiality but is infeasible to explore all attack space. Formal reasoning-based analytics are advantageous for threat analysis, especially for being noninvasive but provable. However, due to the convoluted features and non-linear nature of the system parameters, such formal models also become expensive in solving time, making them unscalable for larger systems. Hence, effective mechanism design is essential to augment the overall performance of the threat synthesis. This work proposes a threat analysis framework, named iAttackGen, where we train generative adversarial networks (GAN) models using the existing stealthy attack dataset (produced from testbed experiments or formal analysis) and generate more attack scenarios. We consider the smart power grid as the reference CPS and stealthy attacks as the threat model. Our evaluation results on standard IEEE bus systems prove iAttackGen’s high accuracy and success rate in synthesizing potential threat vectors.
Md Hasan Shahriar, Alvi Ataur Khalil, Mohammad Ashiqur Rahman, Mohammad Hossein Manshaei, and Dong Chen
2021 IEEE Conference on Communications and Network Security (CNS 2021)
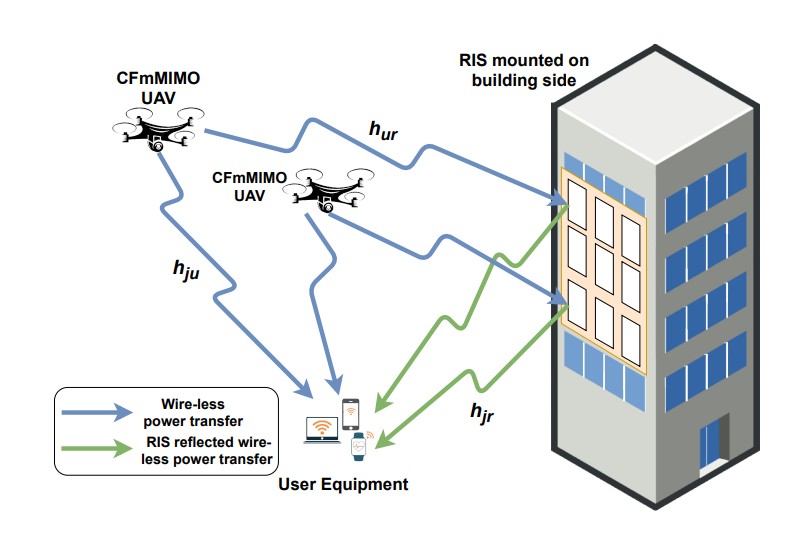
The ever-evolving internet of things (IoT) has led to the growth of numerous wireless sensors, communicating through the internet infrastructure. When designing a network using these sensors, one critical aspect is the longevity and self-sustainability of these devices. For extending the lifetime of these sensors, radio frequency energy harvesting (RFEH) technology has proved to be promising. In this paper, we propose CURE, a novel framework for RFEH that effectively combines the benefits of cell-free massive MIMO (CFmMIMO), unmanned aerial vehicles (UAVs), and reconfigurable intelligent surfaces (RISs) to provide seamless energy harvesting to IoT devices. We consider UAV as an access point (AP) in the CFmMIMO framework. To enhance the signal strength of the RFEH and information transfer, we leverage RISs owing to their passive reflection capability. Based on an extensive simulation, we validate our framework’s performance by comparing the max-min fairness (MMF) algorithm for the amount of harvested energy.
Alvi Ataur Khalil, Mohamed Y Selim, Mohammad Ashiqur Rahman
IEEE 46th Conference on Local Computer Networks (LCN 2021)
Federated deep reinforcement learning-assisted uav trajectory planning against hostile defense system (Pending)
Mohammad Ashiqur Rahman, Alvi Ataur Khalil
US20250224730A1 (2025)
Systems and Methods for Defending Attacks on Transactions of a Blockchain Network (Provisional Application)
Mohammad Ashiqur Rahman, Alvi Ataur Khalil
19/235,187
Non-Interactive Zero-Knowledge Proof-Based Secure Hashed Key Verification for Payment Channel Networks
Alvi Ataur Khalil and Mohammad Ashiqur Rahman
Submitted to IEEE Transactions on Dependable and Secure Computing (TDSC) [Under Review].
DReUS: Deep RL-Enabled UAV Swarm for Post-Disaster Surveillance and Survivor Response
Alvi Ataur Khalil, Syed Ahmad Shah, Mohammad Ashiqur Rahman, Md Yusuf Sarwar Uddin and Abusayeed Saifullah
Submitted to IEEE Transactions on Network and Service Management (TNSM) [Under Review].
xPoz-Hub: Privacy Infiltration in Payment Channel Hubs through Balance Probing and Transaction Discovery
Alvi Ataur Khalil and Mohammad Ashiqur Rahman
2025 Annual Computer Security Applications Conference (ACSAC 2025)
OptiGame: Game-Theoretic Enhancements for Optimistic Rollups through Bayesian Strategies
Alvi Ataur Khalil, Md Golam Moula Mehedi Hasan and Mohammad Ashiqur Rahman
21st EAI International Conference on Security and Privacy in Communication Networks (SecureComm 2025)
Query-Based Model Extraction Attack on GCN: A Surrogate Model Technique for Non-Euclidean Datas
Sibtain Syed, Alvi Ataur Khalil, Kishor Datta Gupta, Saima Jabeen, and Mohammad Ashiqur Rahman
AAAI Fall Symposium Series 2025 (AAAI FSS 2025)
RollGuard: Defending RPC Manipulation Attacks in Optimistic Rollups with Graph ML
Alvi Ataur Khalil and Mohammad Ashiqur Rahman
26th International Symposium on Quality Electronic Design (ISQED 2025)
PARolE: Profitable Arbitrage in Optimistic Rollup with ERC-721 Token Transactions
Alvi Ataur Khalil and Mohammad Ashiqur Rahman
54th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN 2024)
Secured UAV Navigation: A Novel Intrusion Detection System Based on PWM Signal Analysis
Alvaro Alva, Luis Martinez Moreno, Muneeba Asif, Alvi Ataur Khalil, Mohammad Ashiqur Rahman, Alfredo Cuzzocrea, and Shahriar Hossain
2024 11th IEEE Swiss Conference on Data Science (SDS 2024)
Feasibility analysis for sybil attacks in shard-based permissionless blockchains
Tayebeh Rajabi, Alvi Ataur Khalil, Mohammad Hossein Manshaei, Mohammad Ashiqur Rahman, Mohammad Dakhilalian, Maurice Ngouen, Murtuza Jadliwala, and A Selcuk Uluagac
ACM Journal on Distributed Ledger Technologies - Research and Practice 2023
SHiP: Securing Hashed Timelock Contracts in Payment Channel Networks
Alvi Ataur Khalil and Mohammad Ashiqur Rahman
2023 IEEE Conference on Communications and Network Security (CNS 2023)
FAKey: Fake Hashed Key Attack on Payment Channel Networks
Alvi Ataur Khalil and Mohammad Ashiqur Rahman
2023 IEEE Conference on Communications and Network Security (CNS 2023)
Adaptive Neuro-Fuzzy Inference System-based Lightweight Intrusion Detection System for UAVs
Alvi Ataur Khalil and Mohammad Ashiqur Rahman
2023 IEEE 48th Conference on Local Computer Networks (LCN 2023)
Deep learning-based energy harvesting with intelligent deployment of RIS-assisted UAV-CFmMIMOs
Alvi Ataur Khalil, Mohamed Y. Selim, and Mohammad Ashiqur Rahman
Elsevier Computer Networks (Volume 229, June 2023, 109784) 2023
FED-UP: Federated Deep Reinforcement Learning-based UAV Path Planning against Hostile Defense System
Alvi Ataur Khalil and Mohammad Ashiqur Rahman
18th International Conference on Network and Service Management (CNSM 2022)
Trajectory Synthesis for a UAV Swarm Based on Resilient Data Collection Objectives
A H M Jakaria, Mohammad Ashiqur Rahman, Muneeba Asif, Alvi Ataur Khalil, Hisham A. Kholidy, Matthew Anderson, and Steven Drager
IEEE Transactions on Network and Service Management (Volume 20, Issue 1), Published on 10/25/2022
A Literature Review on Blockchain-enabled Security and Operation of Cyber-Physical Systems
Alvi Ataur Khalil, Javier Franco, Imtiaz Parvez, Selcuk Uluagac, Hossain Shahriar, and Mohammad Ashiqur Rahman
IEEE 46th Annual Computers, Software, and Applications Conference (COMPSAC 2022)
FicBit: An improved Fractal Image Compression using Bio-Inspired Techniques
Alvi Ataur Khalil, Al Mahmud, and Asif Ahmed
5th International Conference on Electrical Information and Communication Technology (EICT 2021)
iAttackGen: Generative Synthesis of False Data Injection Attacks in Cyber-physical Systems
Md Hasan Shahriar, Alvi Ataur Khalil, Mohammad Ashiqur Rahman, Mohammad Hossein Manshaei, and Dong Chen
2021 IEEE Conference on Communications and Network Security (CNS 2021)
CURe: Enabling RF Energy Harvesting Using Cell-Free Massive MIMO UAVs Assisted by RIS
Alvi Ataur Khalil, Mohamed Y Selim, Mohammad Ashiqur Rahman
IEEE 46th Conference on Local Computer Networks (LCN 2021)
BIOCAD: Bio-Inspired Optimization for Classification and Anomaly Detection in Digital Healthcare Systems
Nur Imtiazul Haque, Alvi Ataur Khalil, Mohammad Ashiqur Rahman, M Hadi Amini, and Sheikh Iqbal Ahamed
2021 IEEE International Conference on Digital Health (ICDH 2021)
REPlanner: Efficient UAV Trajectory-Planning using Economic Reinforcement Learning
Alvi Ataur Khalil, Alexander J Byrne, Mohammad Ashiqur Rahman, and Mohammad Hossein Manshaei
2021 IEEE International Conference on Smart Computing (SMARTCOMP 2021)